How long personal data is stored on the Internet, what is the shelf life of digital data?

These issues are set daily users, companies and organizations. The answer is simple – a very long time, indefinitely, forever. In fact, things are frequently different, as there are limitations concerning the data, their storage and retrieval, which often determine a particular retention period for digital data.
In matters of data collection, storage and use by third parties the real problem is the transient nature of information. Data collected and stored in one place, can have a validity period in relation to that specific place, but if the data is transferred, lost or stolen and stored from this point on in a new place, their shelf life increases.
How can digital data be stored?

Evernote, an organization that provides services for file sharing and online data storage, guarantees its customers access to their data for 100 years. To fulfill this promise the managers of the company established a trust Fund to ensure the operation of storage server in case the company ended its activity or will be absorbed. Of course, this implies that after 100 years we still will use the same servers and the computers that we use today.
To solve the problem of fast-changing technologies will help, of course, money. If the company can do to be justified from a financial point of view, the ability to transfer data to any modern technology she will be able to continue their activities.
The legality of data retention has been a problem for many countries. In the European Union was adopted the law on data retention, a prerequisite for this was the need to combat crime, but later the law was declared invalid in connection with the violation of basic human rights.
In the United Kingdom, a law was passed with amendments, in the wake of the invalidation of a law enacted in the EU, but he "fell into disgrace" for violation of human rights. He was dubbed "the Charter of the dogs", declaring it an attempt by the government to spy on the population or, worse, an attack on the sources of information that can be used for illegal purposes, for example, for the purpose of fraud.
The United States failed to adopt laws on data retention, binding the Telecom companies and Telecom operators are, however, many private and commercial organizations to actively collect data where they can force the government. The FBI can protect the data by using Letters of National Security, which in fact is a secret warrant, issued without any judicial oversight. Argument: the data can be used to combat crime and terrorism, but the price for that – privacy, civil liberties, and fundamental human rights.
The owners of smartphones sooner or later there is a need for additional storage for the device data: information from your applications, photos, videos, contacts and much more. The need for data backup is caused by many factors, including the desire to keep data safe if:
• an android smartphone in need of repair or need to rewrite apparatus;
• when buying a new model you want to transfer data from your old device;
• there is the risk of loss of the device and therefore the necessary backup for the possibility of recovery on any other device;
• it should print out any data (photos, text documents, etc.).
When deciding how and where to store information from your phone, if Android phone, you must remember that most popular to date for the OS is a cloud service provided by Google. Due to the large volume storage of personal information, availability of office Suite, quick synchronization, cross-platform performance and more, cloud Google today is the most successful from the users. Service called Google Drive has 5 GB free and 10 GB for paid.
The advantages of using Google Drive include the ability to: create various file formats, access data from different devices, OCR scanned pages and photos with text, convert written text into speech record. The main condition – to have an account for Google, if not there, you must first register and create an account.

The usability of Google Drive also and that to use the service as you can with a PC and a smartphone for this purpose was created a mobile client Google Disk. Thanks to simple and tailored navigation application is very easy and differs little from the PC version, the package includes utilities to open the media files and text documents. The app is available on the official website and Google Play Market.
On the topic: how and where to store information from your phone, it is important to think not only about the reliability of the chosen repository, but also how to protect your android smartphone from the interference of outsiders. The best option is to install on the device password. A lot of time and effort it takes, but the importance of such protection is difficult to overestimate. All modern operating systems offer a large selection of locks and give consumers the opportunity to choose any.
However, according to safety experts, such a fashionable and interesting pattern, as well as, other new and interesting ways to lock the smartphone significantly inferior in reliability such traditional options like PIN code or a digital alphanumeric password. Protection of information, which is stored on the mobile device, this is a fairly important set of events, but if for any reason the user ignores them, then it is better not to store on the smartphone personal information to prevent unauthorized access.
When choosing a place to store information it is also important to consider the reliability of the storage, storage terms and conditions, which will be implemented by the storage.
OTHER STORAGE OPTIONS FROM PHONE

Of course, Google Drive is not the only solution to the question, how and where to store information from your phone. With the storage of personal data do an excellent job and traditional storage in the form of hard disks, Flash drives, and cloud and mail services of various companies.
If we talk about hard drives, the lifetime is depending on external factors and the quality of the device from three to ten years. As for flash drives, the average lifetime is about five years if you continue to use the drive at the end of this time, there is a risk that it will fail sooner due to any minor static discharge when connecting to a PC and access to data has become impossible. If you use the drive solely as storage, its service life will be decent and will be up to eight years.
Filling different questionnaires, including the Internet, we don't care about, where we can get our personal information. Even posting your picture online Facebook with the description, the user is not aware that it will be stored on servers outside the country in which he resides.
But is it safe? If we don't pay attention, then of course not. But each of us has such information about our friends and acquaintances. And with each passing day it more and more.
Every day there are new reports of crimes related to theft of personal data. Nevertheless, people do not become less trusting and still continue to store personal data, like your own, without paying due attention to their safety.
Today we often stored our own and others personal data on computers. Of course, store the addresses, phone numbers, email addresses and blogs, as well as information such as passport number, driver's license, and credit card number, it is much more convenient in electronic form.
Reliable protection of personal information and protection of personal data on the phone is a necessity, to avoid a lot of unnecessary problems. Currently, the ways of information security presents a huge number of programs. Unfortunately, not all methods of information protection is quite effective.
The law "On personal data" thus refers to any information that can identify a user. That is, the surname, name and patronymic, date and place of birth, address, marital status, passport details, profession, income and other information. The passwords to the accounts are not personal data because they did not report anything about the person.
With the consent of the user data may become publicly available — for example, telephone number or e-mail, which you submit to company. At the same time the requirement of the user, these data must be removed from public access.
Free Internet and free services, the users pay with data. Large companies like Google and "Yandex" synchronization information from a variety of sources to determine user preferences. They earn on advertising, and the clearer will be the interests of the user, the more accurate the ad to show him. Thus, the user is prompted Facebook sponsored stories based on the pages that he liked, and left information in the public domain.
Sometimes it is necessary to verify your identity when you buy a certain product, but not provided with the necessary documents. What to do in this case? The answer to this question is this: now this is feasible with the help of the project KYC legal on blockchain technology.

This platform, which enables identification of the person(user) and to eliminate thus the deception and fraud.It is based on blockchain technology, i.e. using it as a tool of protection and verification of personal data of people.
What is the function for users:
-all personal information is protected biometric data and using ciphers
-information is stored on the user's device
-everyone chooses the information that is needed for maintenance
-verification of documents with digital sign
What this is useful for services:
- only accurate and truthful information about the person
- no fraudulent and inaccurate information
- KYC (know your customer) compliance
- improvement of the ecosystem of customer interaction and service
You can see this business model in picture:
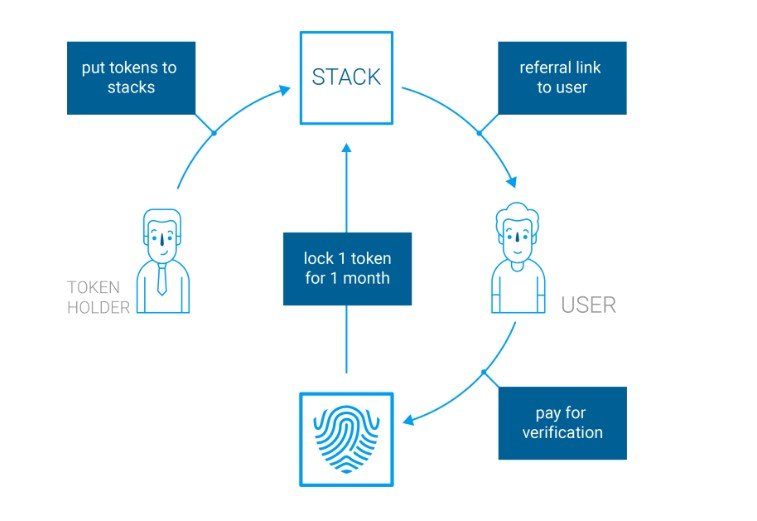
The project plans to establish such cooperation with many companies and their customers. So far only operates the self-test, but soon starts and check with the help of agents that will be sure to pass the procedure of certification. Similar work is carried out, for example, Uber. Uber - is an app that helps drivers and passengers find each other for a few minutes, to quickly and reliably move around the city at any time of the day. No need to park, to wait for a taxi or a bus. With Uber you can order a trip with a single touch and easily pay it by bank card.
KYC token for token holders. KYC token can be used in two ways:
First - traditional “passive” mode designed for any type of token holders - token holders after gaining ownership of tokens can transfer them between wallets or crypto exchanges.
Second - “active” or “stack” mode designed for existing and aspiring service providers. Token holder can create her Stack through a secure profile on KYC.LEGAL platform and store her tokens in there. After tokens are placed in Stack, token holder activates a referral link connected to her Stack. Token holder can place this link on any digital resource.
Price of verification falls between $10 and $50 range per user depending on location and other factors. 50% of
total amount covers the service of certified agent vetted by KYC.LEGAL to complete verification. The remaining 50% is divided between token holder and user based on split ratio defined by token holder.
Every new user verification performed utilizing a provided referral link locks the verification capability of one KYC token from the token holders’ Stack for a month. In a month, this KYC token is unlocked for next verification. The maximum number of verifications performed by one KYC token amounts to 12 per year.
That is, this platform will help you perfectly in these cases: for example when you buy alcoholic beverages or cigarettes and you need to verify your age, or want to make a return, and your documents are at home, then you are using this application, the agent arrives and proves your identity for a fee. Here, everyone wins. The idea is very cool and promising. Participate in the purchase token, or simply use such opportunities.
Site https://kyc.legal
Whitepapper https://kyc.legal/WhitePaper-RUS.pdf
Twitter https://t.me/KYCLEGALru
Facebook https://www.facebook.com/KYCLegal/
My bitcointalk profile https://bitcointalk.org/index.php?action=profile;u=1103736
No comments:
Post a Comment